Xray-Core搭建教程
相关链接
- 一键安装脚本 https://github.com/XTLS/Xray-install
- Xray-Core仓库 https://github.com/XTLS/Xray-core
- 官方文档 https://xtls.github.io/
- 原文 https://idev.dev/proxy/xray.html
- 视频教程 https://www.youtube.com/watch?v=U8Ux7B1RPhY
安装Xray
-
官方的安装方法
-
使用Advance、Install & Upgrade Xray-core and geodata with User=root, which will overwrite User in existing service files
-
安装Xray
cd / sudo su - bash -c "$(curl -L https://github.com/XTLS/Xray-install/raw/main/install-release.sh)" @ install -u root -
查看Xray配置文件
root@xrayr:/# cd /usr/local/etc/xray root@xrayr:/usr/local/etc/xray# ls config.json root@xrayr:/usr/local/etc/xray# cat config.json {} -
查看Xray运行状态
root@xrayr:/usr/local/etc/xray# systemctl status xray.service ● xray.service - Xray Service Loaded: loaded (/etc/systemd/system/xray.service; enabled; vendor preset: enabled) Drop-In: /etc/systemd/system/xray.service.d └─10-donot_touch_single_conf.conf Active: active (running) since Mon 2024-12-16 06:40:27 UTC; 15min ago Docs: https://github.com/xtls Main PID: 90907 (xray) Tasks: 7 (limit: 2349) Memory: 3.9M CPU: 49ms lines 1-10...skipping... ● xray.service - Xray Service Loaded: loaded (/etc/systemd/system/xray.service; enabled; vendor preset: enabled) Drop-In: /etc/systemd/system/xray.service.d └─10-donot_touch_single_conf.conf Active: active (running) since Mon 2024-12-16 06:40:27 UTC; 15min ago Docs: https://github.com/xtls Main PID: 90907 (xray) Tasks: 7 (limit: 2349) Memory: 3.9M CPU: 49ms CGroup: /system.slice/xray.service └─90907 /usr/local/bin/xray run -config /usr/local/etc/xray/config.json Dec 16 06:40:27 xrayr systemd[1]: Started Xray Service. Dec 16 06:40:27 xrayr xray[90907]: Xray 24.11.30 (Xray, Penetrates Everything.) 98a72b6 (go1.23.3 linux/amd64) Dec 16 06:40:27 xrayr xray[90907]: A unified platform for anti-censorship. Dec 16 06:40:27 xrayr xray[90907]: 2024/12/16 06:40:27 [Info] infra/conf/serial: Reading config: &{Name:/usr/local/etc/xray/config.json Format:json} Dec 16 06:40:27 xrayr xray[90907]: 2024/12/16 06:40:27 [Warning] core: Xray 24.11.30 started lines 1-18/18 (END) root@xrayr:/usr/local/etc/xray# -
卸载
bash -c "$(curl -L https://github.com/XTLS/Xray-install/raw/main/install-release.sh)" @ remove --purge
Xray配置文件
https://idev.dev/proxy/xray.html
-
服务端配置文件(带注释)
{ // 日志模块 "log": { "loglevel": "info", "access": "/var/log/xray/access.log", "error": "/var/log/xray/error.log" }, // api模块 "api": { "tag": "api", // HandlerService 用于出入站代理的新增和删除。添加入站代理用户的新增和删除 // LoggerService 支持对内置logger的重启,可以配置logrotate进行日志文件的操作 // StatsService 数据统计服务,可以获取用户的流量数据以及全局的流量数据 "services": [ "HandlerService", "LoggerService", "StatsService" ] }, // 流量统计模块,开启后只需要在policy中启动对应的统计项,用户需要设置email "stats": {}, // 本地策略模块 "policy": { // 开启用户级别为0的用户的流量上下行统计 "levels": { "0": { "statsUserUplink": true, "statsUserDownlink": true } }, // 开启xray进入站代理的上下行流量统计 "system": { "statsInboundUplink": true, "statsInboundDownlink": true, "statsOutboundUplink": true, "statsOutboundDownlink": true } }, // dns模块 "dns": { "servers": [ // 自定义dns服务器,可以解锁流媒体,不需要请删除 { "address": "1.2.3.4", "port": 5353, // 包含的域名优先使用该dns服务器查询 "domains": [ "domain:netflix.com" ] }, "https+local://cloudflare-dns.com/dns-query", "1.1.1.1", "1.0.0.1", "8.8.8.8", "8.8.4.4", "localhost" ] }, // 入站模块 "inbounds": [ // 定义名称为“api”的入站代理 { "listen": "127.0.0.1", "port": 10086, "protocol": "dokodemo-door", "settings": { "address": "127.0.0.1" }, "tag": "api", "sniffing": null }, // 定义vless入站分流代理 { "tag": "vless-tcp-xtls", "listen": "0.0.0.0", // 监听443端口,TLS的入口点 "port": 443, // 协议使用vless才会做后续的回落处理 "protocol": "vless", "settings": { // 用户配置 "clients": [ { "id": "123456", "email": "123456@qq.com", // 指定分流模式,后面“,none”代表兼容普通的tls代理,不需要可删掉 "flow": "xtls-rprx-vision", "level": 0 } ], // 填none ,不能留空 "decryption": "none", // 回落分流配置,目前 XTLS 仅支持 TCP、mKCP、DomainSocket 这三种传输方式 "fallbacks": [ // 回落到web服务的http/1.1伪装服务 { "dest": "172.17.0.2:80", "alpn": "http/1.1", "xver": 1 }, // 回落到web服务的http2伪装服务 { "dest": "172.17.0.2:81", "alpn": "h2", "xver": 1 } ] }, // 底层传输方式设置 "streamSettings": { "network": "tcp", // XTLS Vision 分流模式, 必须是 "tls" "security": "tls", "tlsSettings": { "certificates": [ { // ocspStapling更新间隔,支持证书热更新,提升https性能 "ocspStapling": 3600, // 换成自己的证书,绝对路径 "certificateFile": "/data/cert/latata.me/latata.me.cer", "keyFile": "/data/cert/latata.me/latata.me.key" } ], // 可接受最低的的SSL/TLS版本 "minVersion": "1.2", // 支持的密码套件 "cipherSuites": "TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256", // 如果fallback有h2回落,需要在这添加h2。以下是默认值 "alpn": [ "http/1.1", "h2" ] } }, // 启用流量探测 "sniffing": { "enabled": true, "destOverride": [ "http", "tls" ] } } ], // 出站模块 "outbounds": [ // 定义自由出站 { "protocol": "freedom", "tag": "direct" }, // 定义黑洞出站,禁止访问 { "protocol": "blackhole", "tag": "blocked" } ], // 路由模块 "routing": { // 域名解析策略,默认是AsIs,也就是只使用域名进行路由选择 // IPIfNonMatch 表示域名没有匹配的时候,解析域名为IP再次匹配(一般我会使用该域名解析策略) // IPOnDemand 如果匹配到基于IP的规则,将域名解析为IP进行匹配,最精确,但是很慢 "domainStrategy": "IPIfNonMatch", // 路由规则,从上到下判断。当没有匹配任何规则,流量默认从第一个outbound发出 "rules": [ // 这个是流量进站出站都经过api服务,用来统计流量 { "inboundTag": [ "api" ], "outboundTag": "api", "type": "field" }, // 自定义域名路由到"blocked",用于禁止某些网站的访问 { "domain": [ "domain:iqiyi.com", "domain:video.qq.com", "domain:youku.com" ], "type": "field", "outboundTag": "blocked" }, // 匹配到私有ip以及中国ip则路由到名称为"blocked"的outbound { "type": "field", "ip": [ "geoip:cn", "geoip:private" ], "outboundTag": "blocked" }, // 将bt协议的流量路由到"blocked" outbound { "protocol": [ "bittorrent" ], "type": "field", "outboundTag": "blocked" } ] } } -
服务端配置文件
{ "log": { "loglevel": "info", "access": "/var/log/xray/access.log", "error": "/var/log/xray/error.log" }, "api": { "tag": "api", "services": [ "HandlerService", "LoggerService", "StatsService" ] }, "stats": {}, "policy": { "levels": { "0": { "statsUserUplink": true, "statsUserDownlink": true } }, "system": { "statsInboundUplink": true, "statsInboundDownlink": true, "statsOutboundUplink": true, "statsOutboundDownlink": true } }, "dns": { "servers": [ "https+local://cloudflare-dns.com/dns-query", "1.1.1.1", "1.0.0.1", "8.8.8.8", "8.8.4.4", "localhost" ] }, "inbounds": [ { "listen": "127.0.0.1", "port": 10086, "protocol": "dokodemo-door", "settings": { "address": "127.0.0.1" }, "tag": "api", "sniffing": null }, { "tag": "vless-tcp-xtls", "listen": "0.0.0.0", "port": 443, "protocol": "vless", "settings": { "clients": [ { "id": "739d2e0a-4ef5-46be-a2a8-9ce9cdbf8654", "email": "123456@qq.com", "flow": "xtls-rprx-vision", "level": 0 } ], "decryption": "none", "fallbacks": [ { "dest": "34.146.220.247:80", "alpn": "http/1.1", "xver": 1 }, { "dest": "34.146.220.247:81", "alpn": "h2", "xver": 1 } ] }, "streamSettings": { "network": "tcp", "security": "tls", "tlsSettings": { "certificates": [ { "ocspStapling": 3600, "certificateFile": "/data/cert/vpn.owenweb.cn/vpn.owenweb.cn.cer", "keyFile": "/data/cert/vpn.owenweb.cn/vpn.owenweb.cn.key" } ], "minVersion": "1.2", "cipherSuites": "TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256:TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256" } }, "sniffing": { "enabled": true, "destOverride": [ "http", "tls" ] } } ], "outbounds": [ { "protocol": "freedom", "tag": "direct" }, { "protocol": "blackhole", "tag": "blocked" } ], "routing": { "domainStrategy": "IPIfNonMatch", "rules": [ { "inboundTag": [ "api" ], "outboundTag": "api", "type": "field" }, { "domain": [ "domain:iqiyi.com", "domain:video.qq.com", "domain:youku.com" ], "type": "field", "outboundTag": "blocked" }, { "type": "field", "ip": [ "geoip:cn", "geoip:private" ], "outboundTag": "blocked" }, { "protocol": [ "bittorrent" ], "type": "field", "outboundTag": "blocked" } ] } } -
修改第二点配置,然后添加证书
mkdir -p /data/cert/vpn.owenweb.cn vim /data/cert/vpn.owenweb.cn/vpn.owenweb.cn.cer vim /data/cert/vpn.owenweb.cn/vpn.owenweb.cn.key -
可用xray命令生成UUID
xray uuid 84acadba-734c-43c8-bf91-060386475d48 -
将配置内容复制到config.json
sudo su - cd /usr/local/etc/xray vim config.json -
重启xray
systemctl restart xray.service systemctl status xray.service -
安装防火墙,并开放443端口
firewall-cmd --list-all firewall-cmd --add-port=443/tcp --permanent firewall-cmd --reload firewall-cmd --list-all -
安装docker,然后配置项目NGINX项目
apt install docker.io docker ps docker pull nginx -
添加NGINX的配置文件
cd /usr/local/etc/xray vim docker-nginx-default.conf #文件如下 server { listen 80; server_name vpn.owenweb.cn; location / { default_type text/html; return 200 'hi'; } } -
创建 Docker 容器并挂载配置文件
docker run --name nginx -d \ -v /usr/local/etc/xray/docker-nginx-default.conf:/etc/nginx/conf.d/default.conf:ro \ -p 80:80 \ nginx -
检查 NGINX 配置
docker logs -f nginx
12.进入容器 添加证书
docker ps
docker exec -it nginx /bin/bash
mkdir -p /data/cert/vpn.owenweb.cn
vim /data/cert/vpn.owenweb.cn/vpn.owenweb.cn.cer
vim /data/cert/vpn.owenweb.cn/vpn.owenweb.cn.key
exit13.修改NGINX配置然后项目访问https
vim /usr/local/etc/xray/docker-nginx-default.conf
#修改NGINX配置然后项目访问https
# HTTP 到 HTTPS 的重定向
server {
listen 80;
server_name vpn.owenweb.cn;
location / {
return 301 https://$host$request_uri;
}
}
# HTTPS 配置
server {
listen 443 ssl;
server_name vpn.owenweb.cn;
ssl_certificate /data/cert/vpn.owenweb.cn/vpn.owenweb.cn.cer;
ssl_certificate_key /data/cert/vpn.owenweb.cn/vpn.owenweb.cn.key;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384';
ssl_prefer_server_ciphers on;
location / {
default_type text/html;
return 200 'hi';
}
}13.重启NGINX容器
docker restart nginx- 检查 NGINX 配置
docker logs -f nginx
14.删除和停止容器的命令(可选)
docker stop nginx
docker rm nginx-
浏览器访问vpn.owenweb.cn,页面显示 hi
-
docker监听NGINX访问日志
docker logs -f --tail=0 nginx #输出 # docker logs -f --tail=0 nginx 38.47.125.16 - - [16/Dec/2024:08:30:56 +0000] "GET / HTTP/1.1" 200 2 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Edg/108.0.1462.54" "-" 38.47.125.16 - - [16/Dec/2024:08:30:56 +0000] "GET /favicon.ico HTTP/1.1" 200 2 "http://vpn.owenweb.cn/" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Edg/108.0.1462.54" "-"
14.模拟http1请求
cur -I --http1.1 http://vpn.owenweb.cnnginx伪装配置
- nginx伪装配置
# 只是简单的案例,实现http和http2的回落。根据自己实际情况修改 server { listen 80 proxy_protocol; listen 81 http2 proxy_protocol; server_name vpn.owenweb.cn; set_real_ip_from 34.146.220.247/16; real_ip_header proxy_protocol; location / { proxy_pass https://github.com; proxy_ssl_server_name on; } error_page 500 502 503 504 /50x.html; location = /50x.html { root /usr/share/nginx/html; } }
下载客户端
比如我是Windows就下载Xray-windows-64.zip
地址 https://github.com/XTLS/Xray-core/releases
-
解压安装包,放入到D:\Xray-windows-64
-
然后在改文件夹内创建文件 client.json
将下列客户端配置内容复制到 client.json文件内
-
然后在cmd 执行
cd D:\Xray-windows-64 ./xray -config ./client.json -
设置客户端本地Windows环境的以太网socks代理 地址:127.0.0.1 端口1081
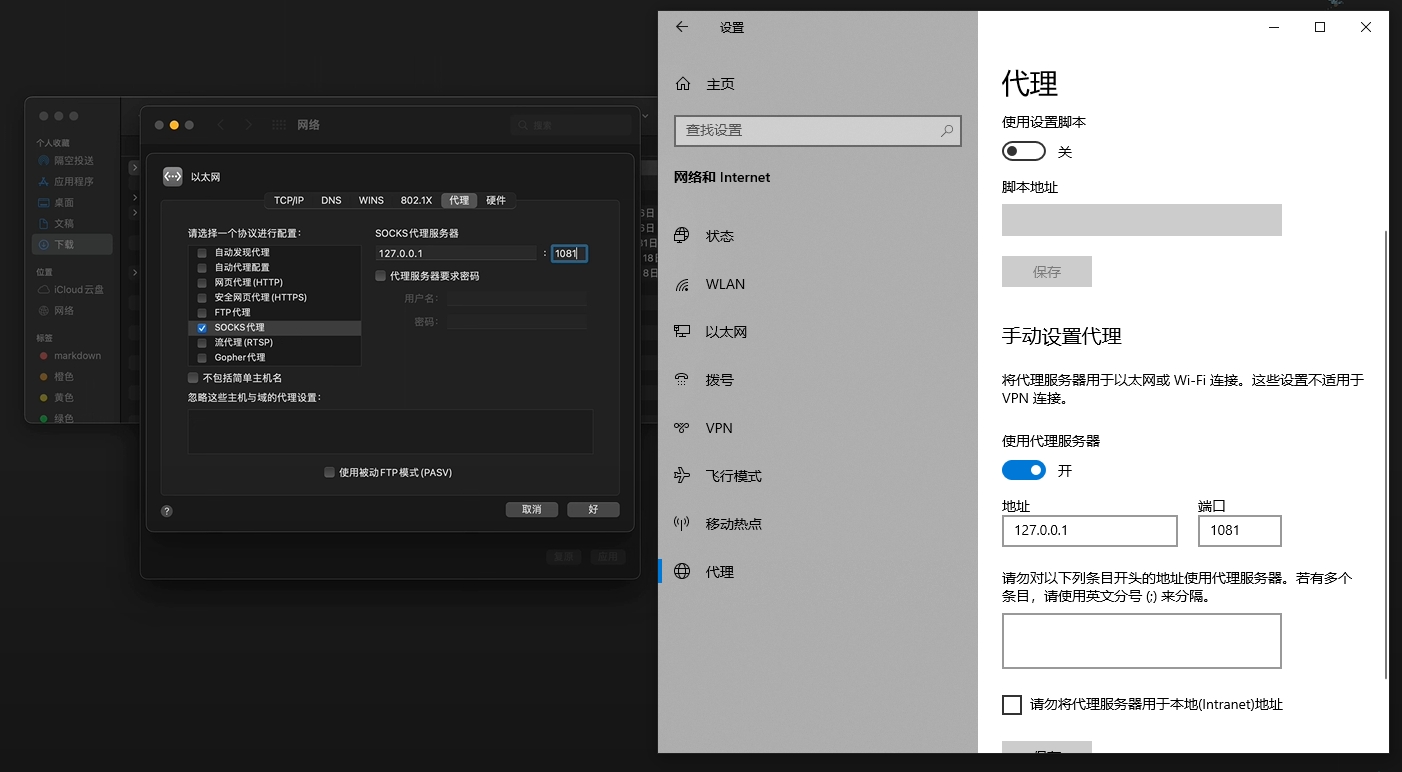
-
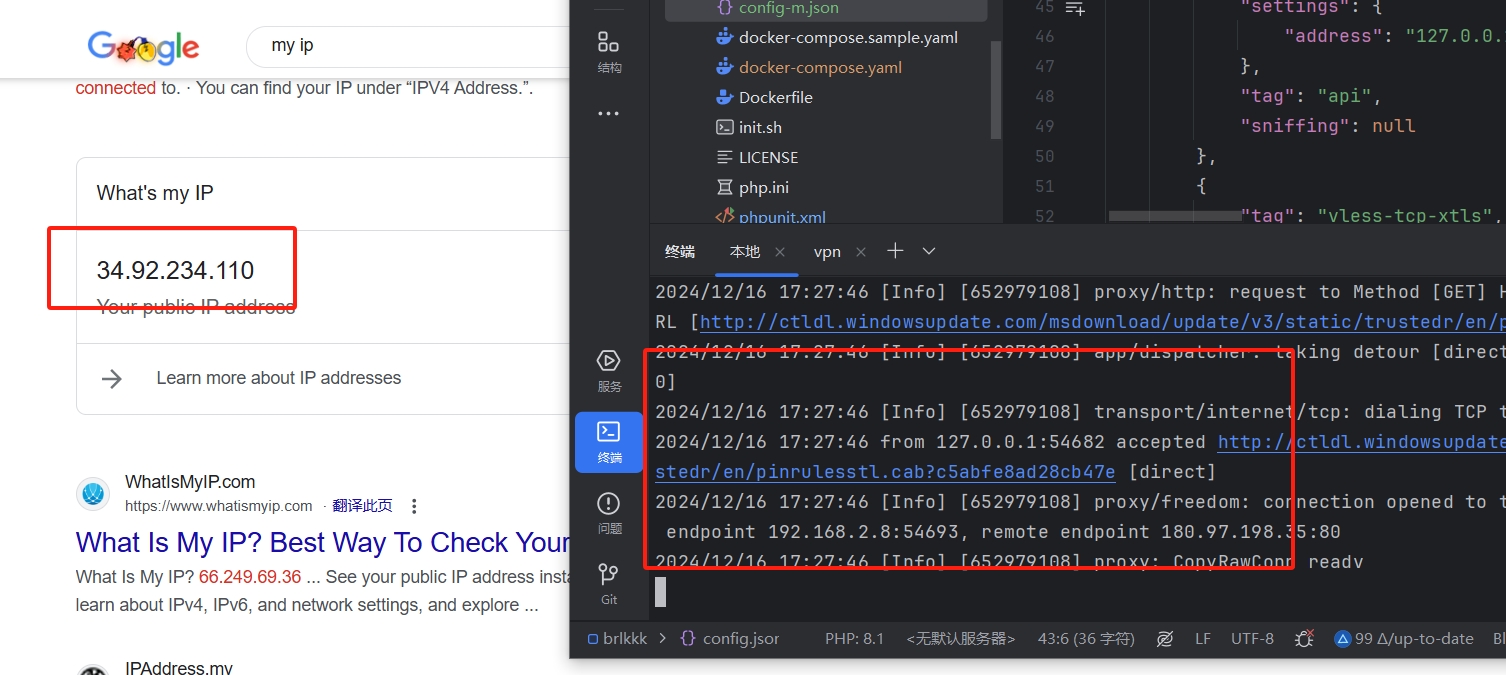
打开Google 搜索my ip 显示34.92.234.110,然后查看本地cmd也在跑
-
VPN设置成功
- 退出cmd,关闭以太网代理,然后设置v2rayN客户端使用
客户端配置
- 客户端配置
{ "log": { "loglevel": "info" }, "routing": { "domainStrategy": "IPIfNonMatch", "rules": [ { "type": "field", "domain": [ "domain:my-proxy.com" ], "outboundTag": "proxy" }, { "type": "field", "domain": [ "domain:my-direct.com" ], "outboundTag": "direct" }, { "type": "field", "domain": [ "geosite:cn", "geosite:private" ], "outboundTag": "direct" }, { "type": "field", "ip": [ "geoip:cn", "geoip:private" ], "outboundTag": "direct" } ] }, "inbounds": [ { "listen": "127.0.0.1", "port": 1080, "protocol": "http", "sniffing": { "enabled": true, "destOverride": [ "http", "tls" ] } }, { "listen": "127.0.0.1", "port": 1081, "protocol": "socks", "settings": { "udp": true }, "sniffing": { "enabled": true, "destOverride": [ "http", "tls" ] } } ], "outbounds": [ { "protocol": "vless", "settings": { "vnext": [ { "address": "vpn.owenweb.cn", "port": 443, "users": [ { "id": "739d2e0a-4ef5-46be-a2a8-9ce9cdbf8654", "encryption": "none", "flow": "xtls-rprx-vision" } ] } ] }, "streamSettings": { "network": "tcp", "security": "tls", "tlsSettings": { "allowInsecure": false, "fingerprint": "random" } }, "tag": "proxy" }, { "protocol": "freedom", "tag": "direct" } ] }
流量统计API使用
- 流量统计API使用
# 获取用户的下行流量 xray api stats --server=127.0.0.1:10086 --name "user>>>123456@qq.com>>>traffic>>>downlink" # 获取用户的上行流量 xray api stats --server=127.0.0.1:10086 --name "user>>>123456@qq.com>>>traffic>>>uplink" # 查看并重置 xray api stats --server=127.0.0.1:10086 --name "user>>>123456@qq.com>>>traffic>>>uplink" --reset # 获取指定inbound|outbound流量 xray api stats --server=127.0.0.1:10086 --name "inbound>>>vless-tcp-xtls>>>traffic>>>uplink" xray api stats --server=127.0.0.1:10086 --name "inbound>>>vless-tcp-xtls>>>traffic>>>downlink"
v2rayN客户端使用
- 添加自定义配置服务器
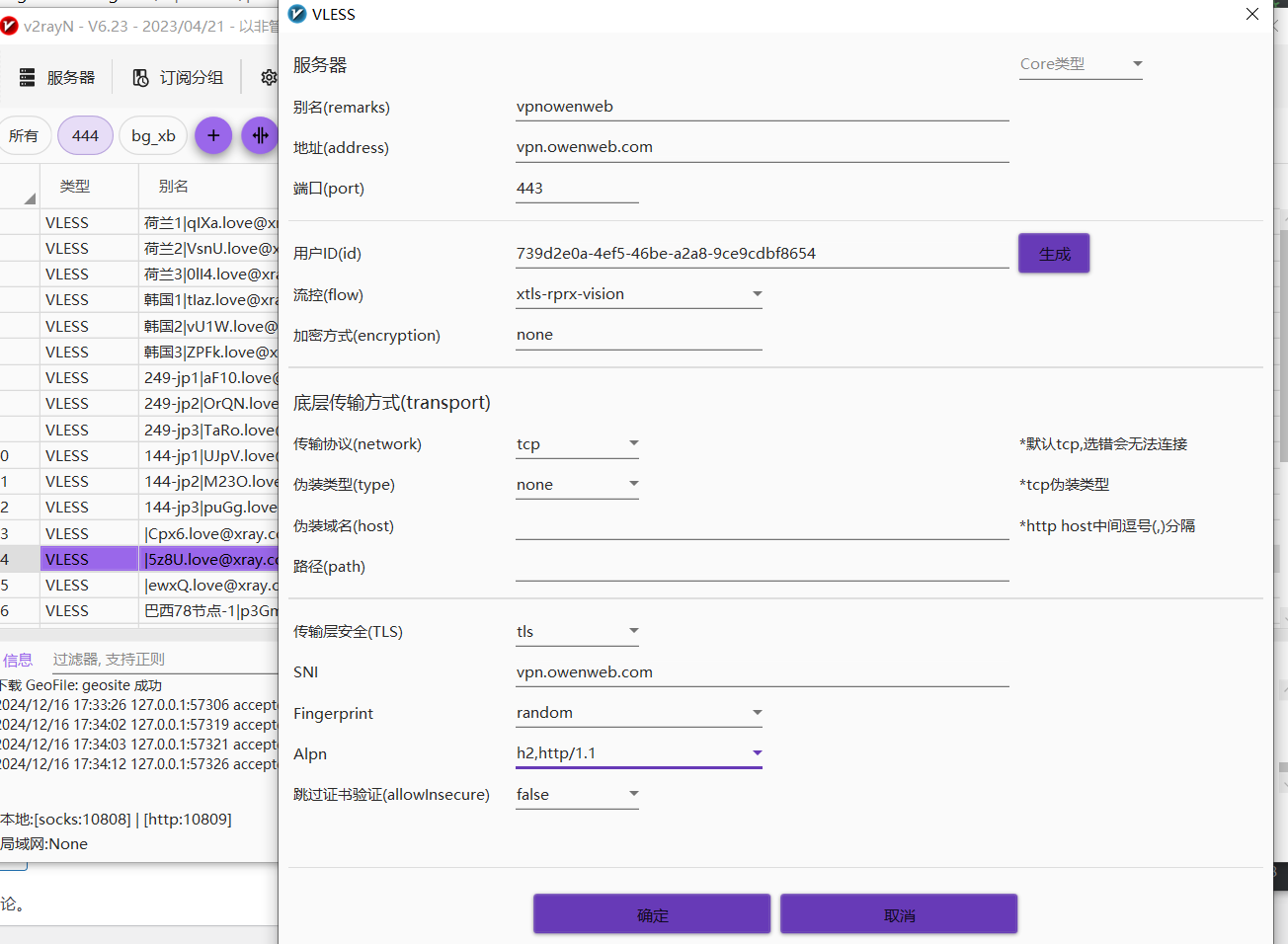
2.设置自动配置系统代理
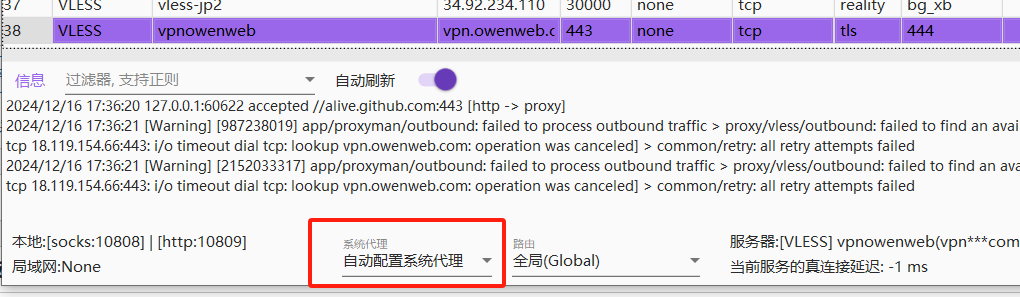
- 浏览Google查看my ip,VPN设置成功

 用户今天 : 22
用户今天 : 22 合计查看 : 16022
合计查看 : 16022 谁是在线的 : 1
谁是在线的 : 1 你的IP地址 : 111.58.85.6
你的IP地址 : 111.58.85.6